Special Instructions:
In the fast-paced world of broadcast news, security goes beyond safeguarding equipment. Newsrooms handle sensitive information, from whistleblower tips to investigative reports. Strong security protocols are essential to protect these sources and the stories that newsrooms produce every day.
Measures can involve everything from access controls to software, control rooms and archives. Ultimately, robust security helps maintain journalistic integrity and data security, and ensures the public receives trustworthy news.
Advancements in Authentication Technologies
Modern web browser authentication technologies have significantly evolved to enhance security and user experience in recent years.
Single Sign-On (SSO) is now a fundamental aspect of the newsroom workflow, empowering users to access multiple applications with one set of login credentials.
The OpenID Connect (OIDC) protocol ensures user authentication with one trusted identity provider (IdP) and access to multiple applications without separate logins. Its compatibility with OAuth 2.0 enables integration across various platforms and services, such as Google, Microsoft Entra ID (formerly Azure Active Directory), and Keycloak, as well as enterprise business applications like Salesforce, Slack, and GitHub.
Securing Broadcast News Operations
Modern newsrooms face significant security threats, with cyber attacks occurring across the globe every 39 seconds, necessitating a proactive approach to security. As broadcasters adopt more digital tools and cloud-based solutions, it is now even more important to ensure the integrity and security of these systems.
Our commitment to helping you work more securely
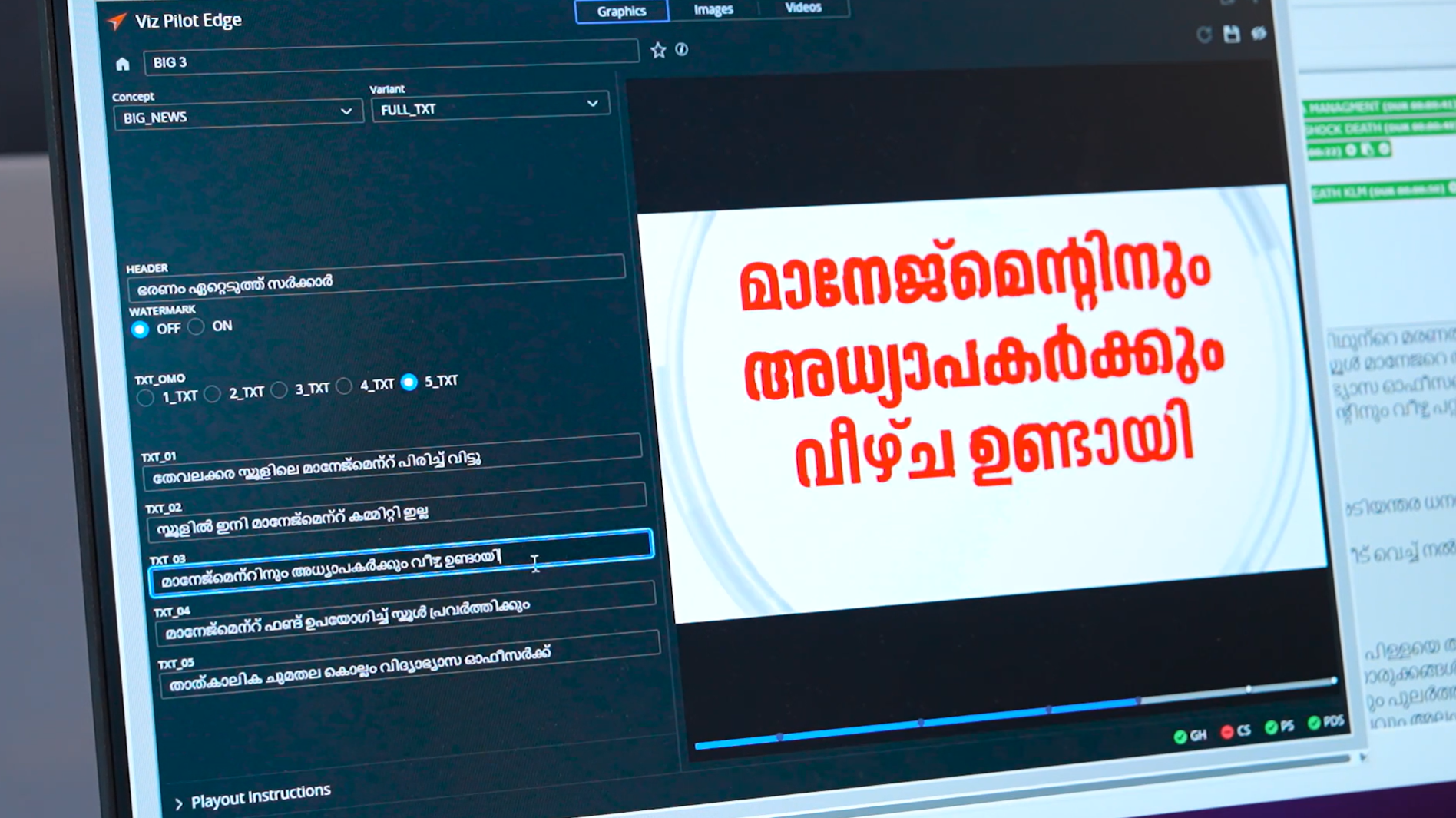
As one of the pioneers in broadcast technologies, we take security very seriously at Vizrt. That’s why we’re excited about the latest version of Pilot Edge, which addresses this need head-on.
In Viz Pilot Edge 3.1, Vizrt introduces user sign-on to our Viz Pilot Edge newsroom computer system (NRCS) plugin, as well as to Template Builder and the Pilot database configuration application. This implementation ensures that only authenticated users can access these applications, enhancing security and user management. Different roles control access levels, and user access is managed through the existing OICD compliant Identity Provider (IdP) system.